Table of Contents
SSH
SSH (Secure Shell) is a protocol, quite similar to Telnet, which allows you to open the command line on a distant computer. SSH is always encrypted - during the establishment of the connection and also during the data transfer. On the destination computer there is a SSH-server and on your own computer there is a SSH-client running. Unix operating systems like Solaris and Linux have SSH as a default. If you have a Windows computer you can use e.g. Cygwin (tutorial). Another option as Windows-client is as mentioned before PuTTY. There more other good alternatives.
For PuTTY there is also an USB-Stick variation which no longer stores the configuration files in the registry, but in individual files
SSH is able to do more. Not only can a distant command line be displayed and operated, but also graphical applications (X-forwarding). It's also possible to forward local and distant ports (Portforwarding) and files can be copied (via Secure Copy, short SCP, or FTP via SSH, short SFTP).
grapihcal programs
If you start a SSH-connection with the parameter -X (or activate the PuTTY X11 forwarding - you can find the latest release in Connection/SSH/Tunnel), the X-applications, which you start via the SSH-tunneled command line, are shown on the local X-server. TO do this there has to be a running X-server - which is not a problem for Unix/Linux. If you are using Windows, there several possibilities, even free one - e.g. with Xming or Cygwin/X.
SSH Server of the RBG/ISP
At the moment there are six SSH login computers of the RBG/ISP active:
- clientssh1.rbg.informatik.tu-darmstadt.de - ProxMox
- clientssh2.rbg.informatik.tu-darmstadt.de - ProxMox
- clientssh3.rbg.informatik.tu-darmstadt.de - ProxMox
- clientssh4.rbg.informatik.tu-darmstadt.de - ProxMox
- clientssh5.rbg.informatik.tu-darmstadt.de - ProxMox
- clientssh-arm.rbg.informatik.tu-darmstadt.de - Hardware ARM
After you failed to login three times your IP adress will be blocked for 5 minutes.
SSH key generation
To generate SSH keys on the Linux-shell:
- for RSA
~$ ssh-keygen -b 4096 -t rsa
- for ECDSA
~$ ssh-keygen -b 384 -t ecdsa
- for ED25519
~$ ssh-keygen -t ed25519
The DSA algorithm should not be used anymore because the lenght of the key is limited to 1024 bit.
This procedure is also recommended for MacOS.
SSH key lenght
Relevant for the security of the SSH key is the lenght which are given in bits. The default setup is 1024 bit which is not so secure anymore. Therefor you should use a lenght of 2048 or 4096 bit.
The lenght can be checked using ssh-keygen:
- for RSA keys
~$ ssh-keygen -l -f ~/.ssh/id_rsa
The number on the beginning shows the lenght of the keys.
SSH help
Further Information on SSH-keys can be found on this page.
SSH help for Putty
If you want to connect to the clientssh computer with a Windows computer you can use e.g. Putty
SSH-key generation
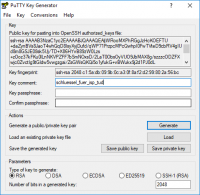
If Putty is installed (e.g. via MSI-Installer for Windows) you can start the key generation with the program PuTTYgen.
You can set up RSA in the default settings. Now you have to click on generate und move the mouse pointer around randomly on the empty surface beneath the progress bar until it finishes.
The key is now generated which can be saved via the button Save private key (best, but not necessarily in C:\Users\<username>\.ssh\). This file must not be passed on!
Now you copy the text in the box under Public key for pasting into OpenSSH authorized_keys file: in the clipboard. After you login in the ISP-accountmanagement with the HRZ-SSO and klick on the button SSH Public-Key registrieren. Now you will receive a mail which contains a link which will direct you to a box where you can enter your Public Key from the clipboard. Now click on SSH-Key übernehmen.
SSH-connection with PUTTY
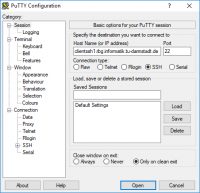
To conact to the pool-computer via SSH with a Windows computer please start PuTTY
You enter under Host Name (or IP address) the above chosen server (e.g. clientssh1.rbg.informatik.tu-darmstadt.de). Below you choose SSH.
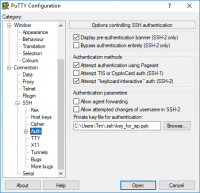
Now you switch on the left side to the section Connection → SSH → Auth and choose under Private key file for authentication: the previously stored private key-files.
Via Window on the left side you can save the settings.
After that you click on open. Now a window opens, in which you compare the fingerprint with the one you find on the website and after that you should confirm that. The console window will open. After entering the TU-ID the connection is establish. You can end the connection with the command exit.
SSH fingerprints
If you want to check your key on our SSH server, you can do this using fingerprints. These are different per software image:
* buster (currently live on clientssh1-5)
ECDSA-256 SHA256:zeKR30Lq/eaPe7eA/cDLuL4IgnyFby1mJ5f33QsGJsQ ED25519-256 SHA256:sQ4CSPUgAAEpdB711AyfnsnRKV/jfoy7uK+LK4OE8pM RSA-2048 SHA256:QBDFW3W5ICxvkbPr3zFHqwE3xLzupEqKYTbGIksQTxo
* arm (clientssh-arm):
ECDSA-256 SHA256:JqsPhgaeQmQff9wHnAEgDOf9NI9XNNt3yA0YU4JRcGE ED25519-256 SHA256:SxplNENSJpd166uoqOVgFYaLtReCrh/sEutx3m37Fz8 RSA-2048 SHA256:bFOBv3pYwIGgTfnxDv0UHEInlLmblCw8meVRDhZWd7k
deploy and upload SSH key Schlüssel
Please deploy your public key via HRZs IDM interface. The old mechanism is still working, but removal is planned for October 2025:
- copy the key to ~/.ssh/authorized_keys on the pol-computer
- upload the key via the webfront of the support. It takes some minutes until the key is stored in the home-directory. (look in the section generating SSH-key)
examples and other tipps
On the subject of SSH-tunnel there is a detailed tutorial written by Thomas Binder, which also includes the creation and use of RSA keys as an alternative for password authentication.
In PuTTY you can find the dialog for setting up the portforwarding in the certain version under Connection/SSH/Tunnels. To do this you make the following set-ups:
- Source port: 8080
- Destination: www.informatik.tu-darmstadt.de:80 and local
This corresponds a portforwarding from the local port 8080 to the port 80 on the www.informatik.tu-darmstadt.de from a remote computer. If you enter localhost:8080www.informatik.tu-darmstadt.de in your browser you will land on the page - but it seems like you come from the computer, on which you have your SSH-connection. Protforwarding only works while there is a SSH-connection.
Secure Copy (SCP)
SCP allows the encrypted copy of files if the destination computer is hosting a SSH-server. This is the case e.g. on the computer clientssh1 and clientssh2 of the RBG/ISP. You can use this fact e.g. to retrieve files from home or transfer them on one of the computers at the university.
- some examples:
| command | meaning |
|---|---|
| scp talk.pdf user@clientssh1: | copy talk.pdf (local) in the home-directory of the User user (Uni) |
| scp talk.pdf user@clientssh1:/media/tmp/user | copy talk.pdf (lokal) in the temporary directory of the User user (Uni). This must exist or talk.pdf will be renamed in user (Uni) |
| scp user@clientssh1:tutorial2.pdf /tmp | copy tutorial2.pdf from the home-directory of the User user (Uni) into /tmp (local) |
| scp user1@clientssh1:info.txt user2@clientssh1: | copy info.txt from the home-directory of the User user1 (Uni) in the home-directory of the User user2 (Uni) |
You have to enter the password for the given user in every case. clientssh2 can also be used instead of clienstssh1.
SFTP und FTPS
SFTP is FTS via SSH. This variant is also supported. Clients are e.g. WinSCP or gFTP (look above). Please keep in mind that entries in .bashrc and similar files (e.g. .profile) might lead to a failing connection establishment. Specifically, this can be output with echo or another shell.
FTPS on the other side means FTP via SSL or TLS. This access type is not supported.
programs
Under UNIX/Linux most people use the command line programs ssh for the connection establishment (with portforwarding if necessary, take a look in the tutorial for ssh-tunnel) and there is also scp installed. As graphical alternative you can use gFTP (with OpenSSL-bindings); KDE-prgorams like Krusader can also use the KIO-slaves fish for SCP- and sftp for STFP-access (fish:user@host and sftp:user@host)
Under Windows you can use the PuTTy-package equivalent command line program for the file transfer like pscp. It's more comfortable to use WinSCP, which is a graphical application that also supports SCP and SFTP (but not FTP!).